#IDP#SSO
While both Single Sign-On (SSO) and Federated Identity Management (FIM) are closely related, they are not the same. Single Sign-On (SSO) allows users to access multiple services or applications with a single login within a single organization. Federated Identity Management (FIM) goes a step further by enabling secure access across multiple systems or enterprises. FIM is a broader framework that connects two identity management systems securely and seamlessly. In this blog, we’ll explore SSO and Federated Identity Management, how they improve access and security, the role of IdPs, and the protocols supporting federated authentication. We’ll also discuss the growing need for secure identity management in today’s interconnected world.

As businesses increasingly rely on a growing array of digital services and platforms, the complexity of managing user identities across different applications has become a major challenge. As data security is essential, organizations need a solution that ensures secure, seamless access to their systems while preventing unauthorized entry.
The rise of remote work, cloud computing, and mobile applications has expanded the number of touchpoints where users interact with services, making it more difficult to manage multiple identities. Traditional methods of password management no longer suffice. Users are overwhelmed with numerous credentials, and businesses are facing heightened risks of data breaches and compliance failures.
FIM addresses these challenges by allowing users to authenticate once and gain access to multiple systems, both within and outside an organization. This reduces the burden of managing credentials and strengthens security, as the authentication process is handled centrally by trusted identity providers. By securely linking identities across different platforms, FIM provides organizations with greater control, flexibility, and efficiency.
Our online identities are a maze of user names and credentials. Each time we use a website or service, we need to create an online identity. For organizations, this means creating multiple credentials for employees and customers each time a new application is deployed. Ultimately, users and employees have too many identities and passwords to remember. This leads to security issues like weak password hygiene that compromises businesses and individuals alike.
As a result, organizations need to enable users with simplified access for all their apps using SSO and FIM. This is typically done with the help of an Identity provider (IdP) - a trusted provider that enables the access of SSO and other technologies to manage identities. However, there are many differences between FIM and SSO and different use cases for each solution. Here’s taking a look at these in detail:
Single-sign-on helps users access various web apps at once with just a single set of credentials. For enterprises that need multiple apps for HR, payroll, communications, project management etc, an SSO approach lets employees access these services using a single set of credentials.
This allows users to do their job easily without having to remember multiple passwords, making errors, using compromised passwords etc. It also reduces IT resources and spends on password resets and support.
But in addition to internal use, businesses can leverage SSO to help customers use various sections of an account. An example of this: retail networks with many brands use SSO to allow customers to access their accounts for multiple stores using one single dashboard. When users shuttle between each store, the site re-authenticates customers with the same credentials.
SSO is a subset of Federated Identity Management. FIM is a set of protocols that helps enterprises and apps share user identities. It is an arrangement that scales beyond a single company to multiple apps and companies so that users leverage the same set of identifiers to use many applications.
Therefore, it is FIM that allows you to sign in to Spotify with your Facebook login details. But how does authentication work in the federated model? The responsibility of verifying and authenticating user ids and passwords lies with the identity provider (IdP) and not the applications. So, when users attempt to log into specific apps or service providers, the app then communicates with the IdP to authenticate the user. The process of user identity authentication is executed using protocols such as Security Assertion Markup Language (SAML), or OpenID Connect or OAuth 2.
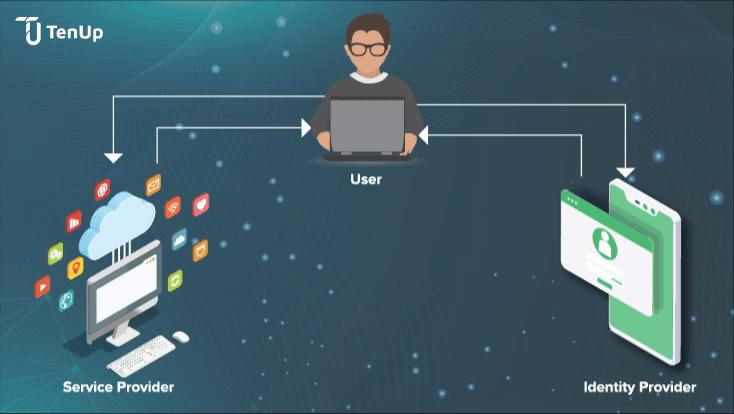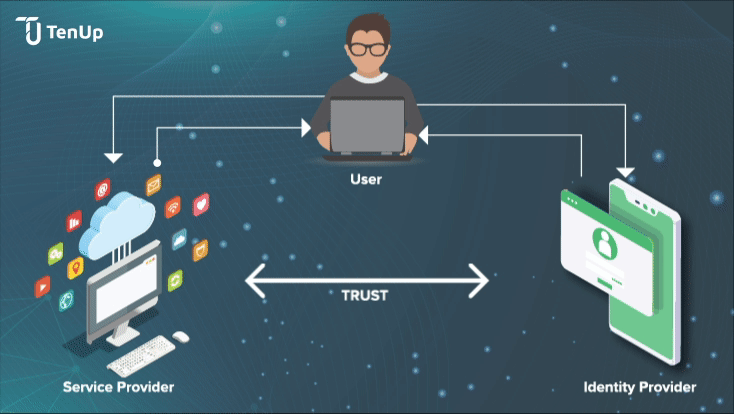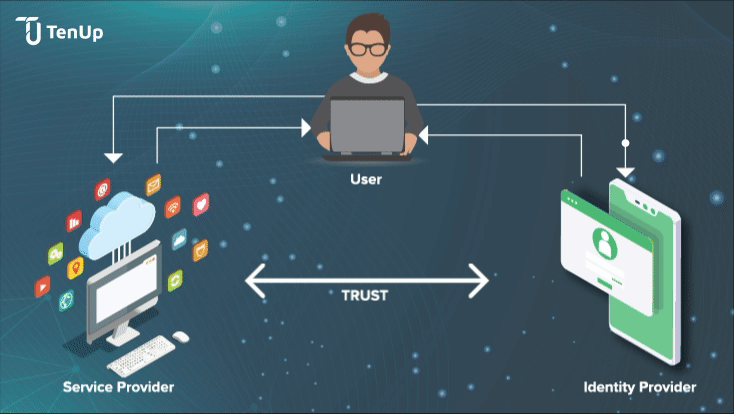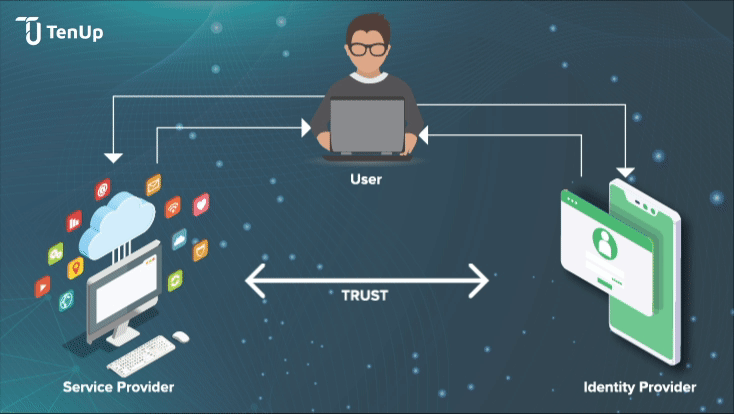
How does Identity Federation work in practice? Let’s say a user wants to access a secured application that needs user authentication. This is what happens:
At TenUp, we’ve applied FIM across our own product suite, streamlining authentication and user access. To see how we put these principles into action, check out our case study.
Identity Providers (IdP)s are trusted 3rd party vendors that create and manage user identities for an organization along with associated attributes. One of the main advantages of IdPs is authentication for third-party service providers like websites, apps etc by federating user identities and authenticating the end-users to service providers without using actual login details.
This is also known as Bring Your Own Identity (BYO). IdPs help manage identities of varying degrees of strength and identity attributes including those for social networks, banks, mobile network operators, governments, digital identity providers etc.
There are multiple Open Source IdPs(OpenAM, Keycloak) and Proprietary IdPs(Okta, AuthO, OneLogin, Redhat/IBM Identity and access management) that enterprises can leverage to manage and secure user authentication and build identity controls.
Some of the leading websites and services use OpenId, SAML and OAuth for identity federation.
OAuth is an open-standard protocol for authorization that enables apps with the ability for secure designated access. Where SAML uses XML, OAuth uses JSON and provides a simpler mobile experience. For mobile apps, modern web, gaming, and Internet of Things (IoT) devices, OAuth offers a better user experience compared to SAML.
OAuth 2.0 is a framework that controls authorization to a protected resource. OpenID Connect and SAML are both industry standards for federated authentication.
OpenID Connect is an open standard built on the OAuth 2.0 protocol, It is sponsored by Facebook, Microsoft, Google, Ping Identity, PayPal, Symantec, and Yahoo. It helps users to be authenticated with 3rd party identity providers. Users can select their own OpenID providers to access websites that use the OpenID authentication system.
SAML is an open standard that enables IdP to pass credentials to SP using XML data format. Iit is independent of OAuth and uses XML SAML format as opposed to JWT. SAML helps secure web domains exchange user authentication and authorization data. It is one of the most popular open standards because of its efficiency and speed in accessing multiple apps through assertion.
Identity federation can be the key differentiator for application vendors catering to large enterprises with strict compliance and security requirements. Potential customers will look for a secure authentication system, and identity federation wins major brownie points from most CTOs and CISOs.
Identity federation can help automate many manual processes in a secure identity framework to help deliver revenue-boosting services to customers. In addition, many companies want to outsource certain areas of operations so they can focus on their core activities. With identity federation, businesses can easily hand over these operations to partners without fearing information and security breaches.
In today’s globally connected landscape, there is immense value in establishing and managing identities within organizations, across enterprises and for individuals globally. Identity Management paves the way for innovation with little or no friction.
Effective identity management and security are not only business and privacy requirements, they are also key to a company’s digital transformation efforts.
Managing user access and security is becoming more important as businesses use more online services. We’ve already discussed in detail the concepts of SSO, FIM, IdPs, their protocols, and why businesses need them.
At TenUp, we’ve worked with many businesses to implement secure, scalable identity management solutions using FIM. Please check out our success story where we applied military grade security using splitkey cryptography to secure an enterprise-grade software product. Our team can help you integrate IdPs, manage user access across multiple platforms, and simplify your IT security. If you're ready to take your identity management to the next level, we’d love to help you find the right solution.