#SAAS#MultiTenancy
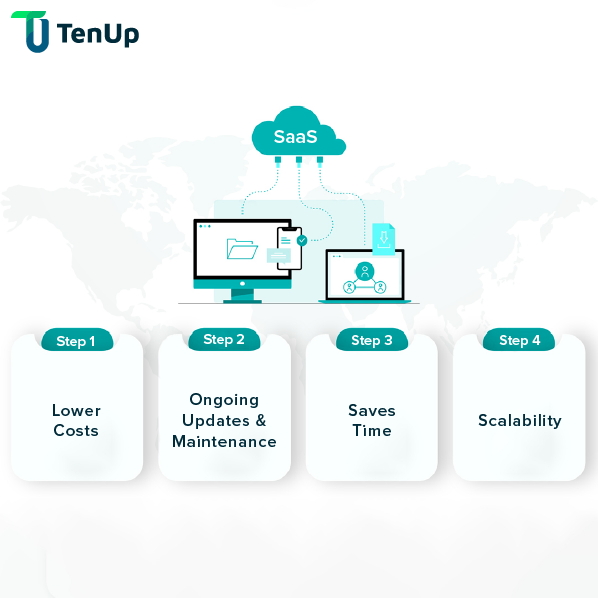
In cloud based Software as a Service systems with multi-tenants have transformed how businesses access and use the software. Multi-tenant SaaS applications provide cost-efficiency, scalability, and simplicity of access by serving numerous clients from a single application instance.
This article delves into the notion of tenant data isolation and offers essential factors, effective data separation solutions, security and access controls, as well as the privacy and compliance concerns connected with working in multi-tenant environments.

In the context of a SaaS application, a tenant refers to an individual or organization that uses the application as a customer or user. Multiple tenants use the same application instance while maintaining independent data and settings. This enables SaaS providers to service numerous customers effectively while still providing security, privacy, and customization choices for each tenant.
With the pooling of resources and infrastructure, however, preserving the isolation and security of tenant data becomes critical. Tenant data must be adequately protected not only to maintain customer trust but also to comply with data protection rules and mitigate security threats.
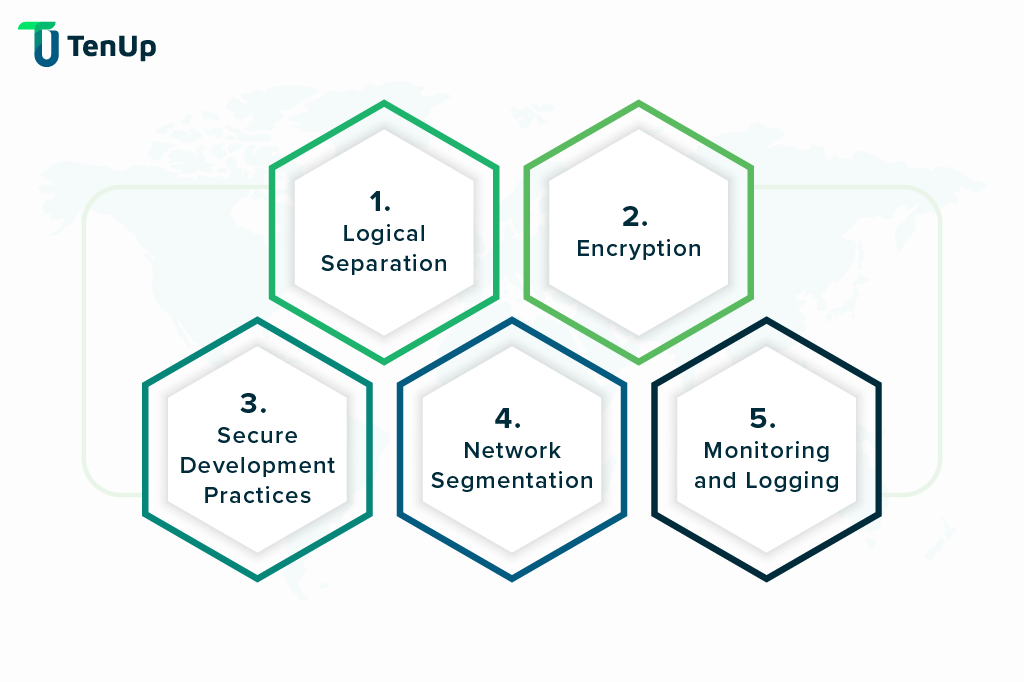
Database Level: Employ techniques like shared schema, schema-per-tenant, database-per-tenant to logically separate tenant data and prevent unauthorized access.
Access Controls: Implementing strict authentication and authorization mechanisms to ensure that tenants can only access their data
In a SaaS application, encryption plays a crucial role in ensuring the security of data. Here are a couple of points related to encryption:
All data, including files like documents, photos, and videos, is secured using either a shared key or a tenant-specific key. This encryption takes place at the block level for storage systems such as EBS (Elastic Block Store) or comparable, and at the object storage level for systems such as S3 (Simple Storage Service) or equivalent.
An additional layer of encryption is applied to sensitive data kept at the column level, corresponding to each tenant. This encryption is accomplished through the use of either a shared key or a tenant-specific key. Individual fields or attributes holding sensitive information are protected by encrypting at the column level, guaranteeing that even if unwanted access happens, the data remains encrypted and unreadable without the right decryption key.
Code Review and Audits: Conduct regular security audits and code reviews to identify and address vulnerabilities.
Isolation Measures: Implementing network segmentation (only used for a few use cases and are not required for major Saas based systems), firewalls, and network access control lists (ACLs) to restrict access between tenants and protect against unauthorized traffic
Centralized Logging: Generate secure logs for multi-tenant applications, analyzing and monitoring events like authentication, access control modifications, and data access.
Security Information and Event Management (SIEM): Implement a SIEM solution to analyze log data from multiple sources, identify patterns, detect anomalies, and monitor security incidents proactively.
Real-time alerts: Real-time alerts are crucial in multi-tenant applications for timely security responses. They detect illegal access to cross-tenant data and are triggered by predefined rules or anomaly detection algorithms. Integration with incident response processes and automation streamlines the mitigation process and reduces the impact of security breaches.
To accomplish tenant data separation, different database strategy design alternatives are available.
Each approach has its own set of pros and cons, depending on criteria such as the application's nature, scalability needs, and desired amount of data isolation. These design alternatives lay the groundwork for assuring data privacy, security, and compliance in a multi-tenant environment.
In this technique, all tenants share the same database, but each record is associated with a tenant identifier. When querying the database, the tenant identifier is utilized as a filter to ensure data isolation between tenants.
Each tenant has a dedicated database using this technique. This provides the most data separation but is more resource-intensive and may necessitate more maintenance.
As a cloud services company, we understand that this strategy allows each tenant to have their own database schema within the same database. The schema divides the tables and objects associated with each tenant, allowing for logical isolation.
This cloud software solution involves employing database row-level security mechanisms to restrict access to specific rows of data based on the tenant context. This enables numerous tenants to access the same database while maintaining data separation.
Horizontal partitioning divides data horizontally depending on predefined criteria such as a tenant, geographical region, or range of values. Each partition stores a portion of data, and partitions might be kept on various servers or storage systems. This method aids in the distribution of data and workload among many resources, resulting in improved performance and scalability.
is the process of separating a table vertically depending on columns or properties. Instead of keeping all attributes for a specific object in a single table, related attributes are maintained in distinct tables. When certain qualities are accessed more frequently than others, this method can be advantageous since it allows for more efficient data retrieval and improves performance.
Incident response protocols are essential for organizations to manage and mitigate security issues. They involve discovery, triage, containment, eradication, and recovery stages.
In cloud software solutions, the initial detection of security issues involves monitoring systems, while containment measures limit the scope and prevent future damage. Eradication focuses on root causes, and recovery restores systems to normal operation. These practices improve security posture and efficiency.
Here are some significant privacy and compliance considerations in multi-tenant environments:
Cloud software solutions with tenant data isolation as a core feature give consumers peace of mind that their data is safeguarded and isolated from other tenants, assuring confidentiality and compliance with data privacy standards.
At TenUp, we are committed to continuously enhancing tenant data isolation and security, building trust, protecting sensitive information, and ensuring a secure future for SaaS environments. Explore our cloud development services to learn how we can help you build secure, scalable applications with robust tenant data isolation.